Detect-Phish
The Detect-Phish platform empowers organizations to proactively identify and respond to phishing threats, leveraging detection rules, threat intelligence, and AI-powered modules. It enables seamless detection, reporting, and response to phishing and spam emails through employee reporting, analyst uploads, or API integrations. Additionally, it monitors the dark web for compromised business email credentials, contributing to a comprehensive risk assessment.
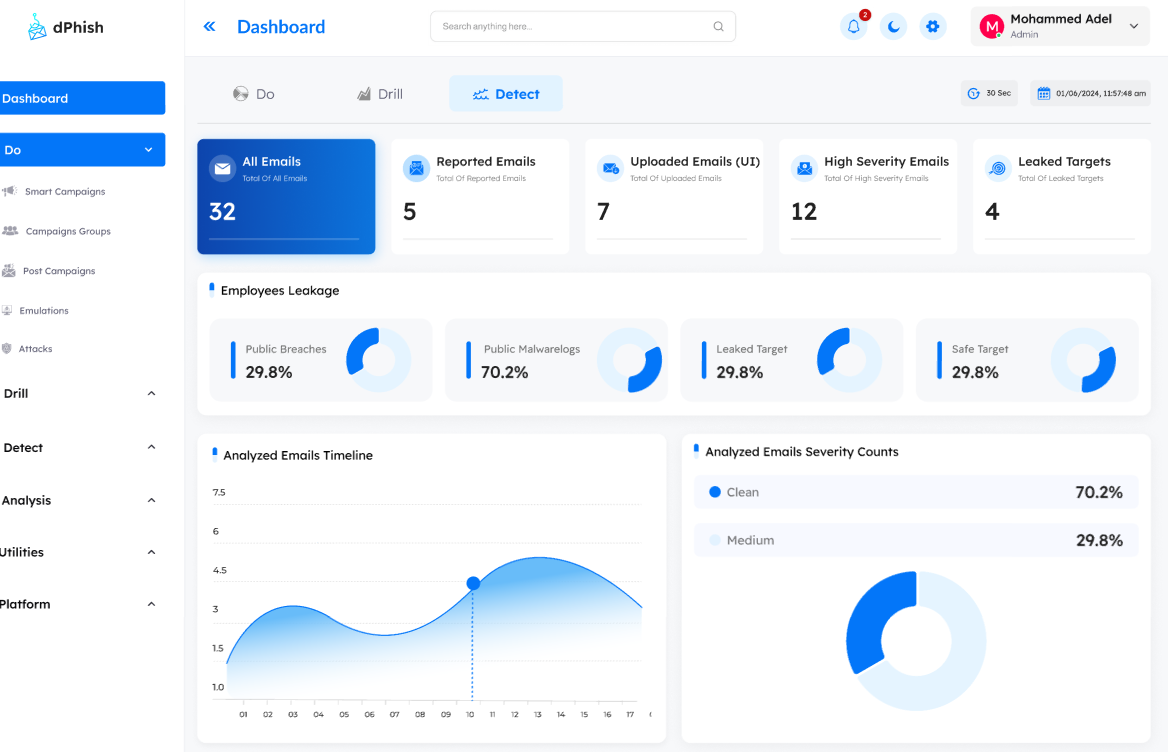

Phishing Detection & Response
Detect-Phish combines advanced technologies to detect phishing emails, enhance employee awareness, and mitigate threats effectively.
- Rule-Based Detection: A robust rule engine supports a wide range of use cases for identifying phishing emails with high accuracy.
- JSON Schema Conversion: Converts reported emails into JSON format, enabling the analysis of all email components, including headers, body, links, attachments, and embedded content.
- Threat Intelligence Integration: Scans observables in emails (e.g., domains, links, attachments) to determine associations with known adversaries.
- Continuous Rule Optimization: The dPhish R&D team regularly updates detection rules to minimize false positives and maximize detection accuracy.
- Adaptive Awareness: Provides real-time feedback if a reported email is part of a phishing simulation to enhance user learning. Sends awareness feedback for genuine phishing cases to reinforce employee vigilance.
- Real-Time Reporting: Enables employees to report phishing emails effortlessly using an intuitive plugin interface.
- Multi-Platform Compatibility: Integrates seamlessly with platforms like Office365, Exchange, and Google Workspace.
- Email Management: Admins can delete or quarantine suspicious emails organization-wide, mitigating risks effectively.
- Email Scoping: Enables admins to analyze the reach of phishing emails by sender, subject, or a combination of both.
- Public Breach Alerts: Identifies business emails exposed in public data breaches.
- Malware Log Analysis: Highlights compromised email credentials found in malware logs with detailed reports, including malware paths, OS versions, and credential samples.
- Continuous Dark Web Scanning: Regular scans against a vast dark web database ensure timely alerts for newly compromised assets.
Benefits
Enhanced Threat Detection
- Detect-Phish ensures comprehensive detection of phishing emails using a combination of rule-based analysis, threat intelligence, and AI modules, minimizing false positives and maximizing accuracy.
Increased Employee Awareness
- Real-time feedback through the reporting plugin boosts employee vigilance and awareness, creating a stronger first line of defense.
Streamlined Response
- Admins can swiftly scope, quarantine, or delete phishing emails, reducing the potential impact of threats and safeguarding organizational assets.
Comprehensive Insights
- Detailed reports and dashboards provide actionable intelligence for identifying vulnerabilities and tracking improvement over time.
Regulatory Compliance
- Ensures proactive cybersecurity measures, supporting compliance with industry regulations and standards.
Proactive Risk Management
- By monitoring the dark web, organizations gain insight into compromised credentials, helping them take proactive measures to mitigate risks before they escalate.