Do-Phish
Phishing Simulation
A comprehensive platform designed to assess employee awareness and test the resilience of email security controls through advanced phishing simulations and adversary emulation.
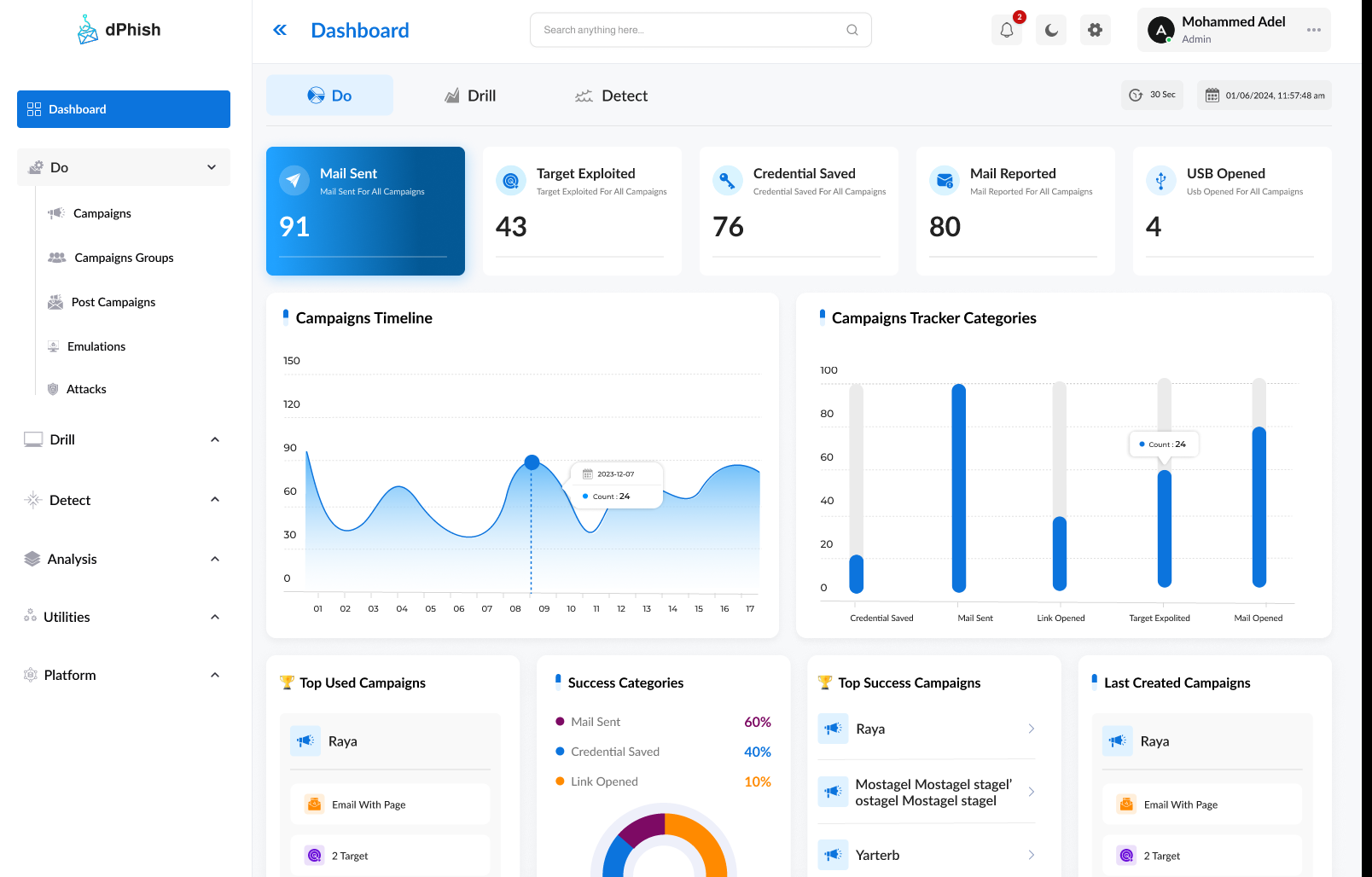

Campaign Preparation
Easily design, customize, and execute sophisticated phishing campaigns.
Launch campaigns using diverse phishing methods, including
- Email with a landing page
- Email with an attachment
- Email with a QR code
- SMS phishing (Smishing)
- Printable QR codes
- HID-based attacks
- USB-based phishing

Access an out-of-the-box template library with culture-driven email templates and landing pages. Options to
- Customize and edit templates
- Clone existing templates
- Create new templates using AI tools

Select senders from Do-Phish's large server farm. Capabilities include
- Sender spoofing
- Advanced sender customization

Target employees based on
- Title, department, manager, location, organization, etc
Automatically execute follow-ups based on user behavior
- Group users by awareness levels
- Tag users based on actions (e.g., link opened, credentials submitted)
- Assign training courses or awareness emails tailored to individual interactions
Features
The phishing simulation component of Do-Phish serves as a strategic tool to proactively strengthen an organization’s cybersecurity framework by addressing one of the most common vulnerabilities: human error. It also provides a comprehensive awareness assessment, allowing organizations to evaluate and enhance employee resilience against phishing threats. Here’s why it’s vital for executives to prioritize this initiative
Campaign Tracking
- Email receipt
- Email open
- Link click
- Credentials submission
- Document opening
Campaign Reporting
-
Generate Executive PDF Reports:
Customizable branding (e.g., colors, logo, headers, footers) -
Option to include recommendations
Access full activity reports in multiple formats (CSV, Excel, JSON). - Customize specific reports for unique use cases with support team assistance
- Group campaigns for comprehensive quarterly reports.
Adversary Emulation
The adversary emulation component of Do-Phish is designed to provide executives with a strategic approach to proactively test and enhance their organization’s cybersecurity defenses. By simulating real-world threats, this tool goes beyond standard testing, offering actionable insights to bolster prevention, detection, and response mechanisms. Here’s why adversary emulation is critical for executives
Preloaded Attack Scenarios
Out-of-the-box payloads (attachments, links) to replicate adversary tactics.
Custom Payload Integration
Add and deploy new payloads as per unique organizational needs.
Delivery Tracking
Monitor email delivery success rates across targeted systems.
Advanced Reporting
Visualize results and performance metrics in intuitive dashboards.
Benefits
Comprehensive Simulation Capabilities
- Fully customizable campaigns aligned with organizational and cultural contexts.
Culture-Driven Template Library
- Modify, clone, or create templates easily using built-in customization tools and AI assistance.
Post-Campaign Improvement
- Build long-term awareness with grouped campaigns and quarterly reports for sustained improvements.
Advanced Tracking and Reporting
- Collect detailed data such as user location, device information, and activity sequence to understand behavior. Customizable executive PDF reports with branding options and in-depth datasets for analysts (CSV, Excel, JSON).
Adversary Realism
- Includes out-of-the-box attack scenarios and custom payload capabilities for flexibility and depth.
Cost-Effectiveness
Ease of Use and Automation
- Automated post-campaign workflows such as grouping users by performance, tagging user actions, assigning courses, and sending awareness emails.