Introduction
CVE-2024-21413 is a vulnerability in the Microsoft Outlook application discovered by Checkpoint Research. Its impact ranges from leaking the local NTLM credentials to remote code execution by abusing how Outlook parses URLs.
Analysis
According to the analysis performed by Checkpoint Research, the vulnerability manifests in how Microsoft Outlook parses different URLs. An attacker can craft a malicious file protocol URI that locates a remote resource on an attacker-controlled server. When the victim clicks on the URI, Microsoft Outlook automatically fetches and parses the resource, using SMB, which can at the very least leak the local NTLM credentials.
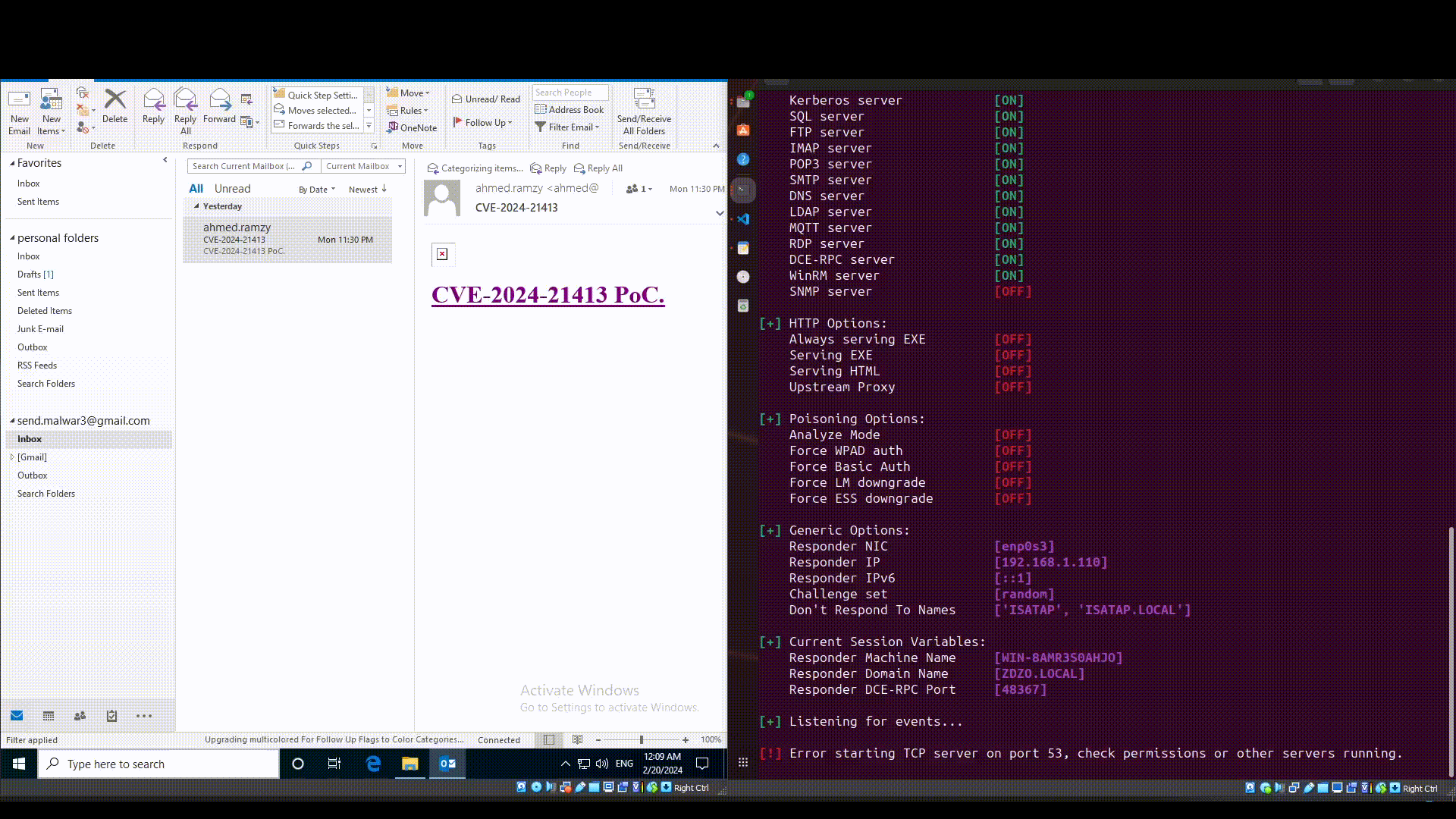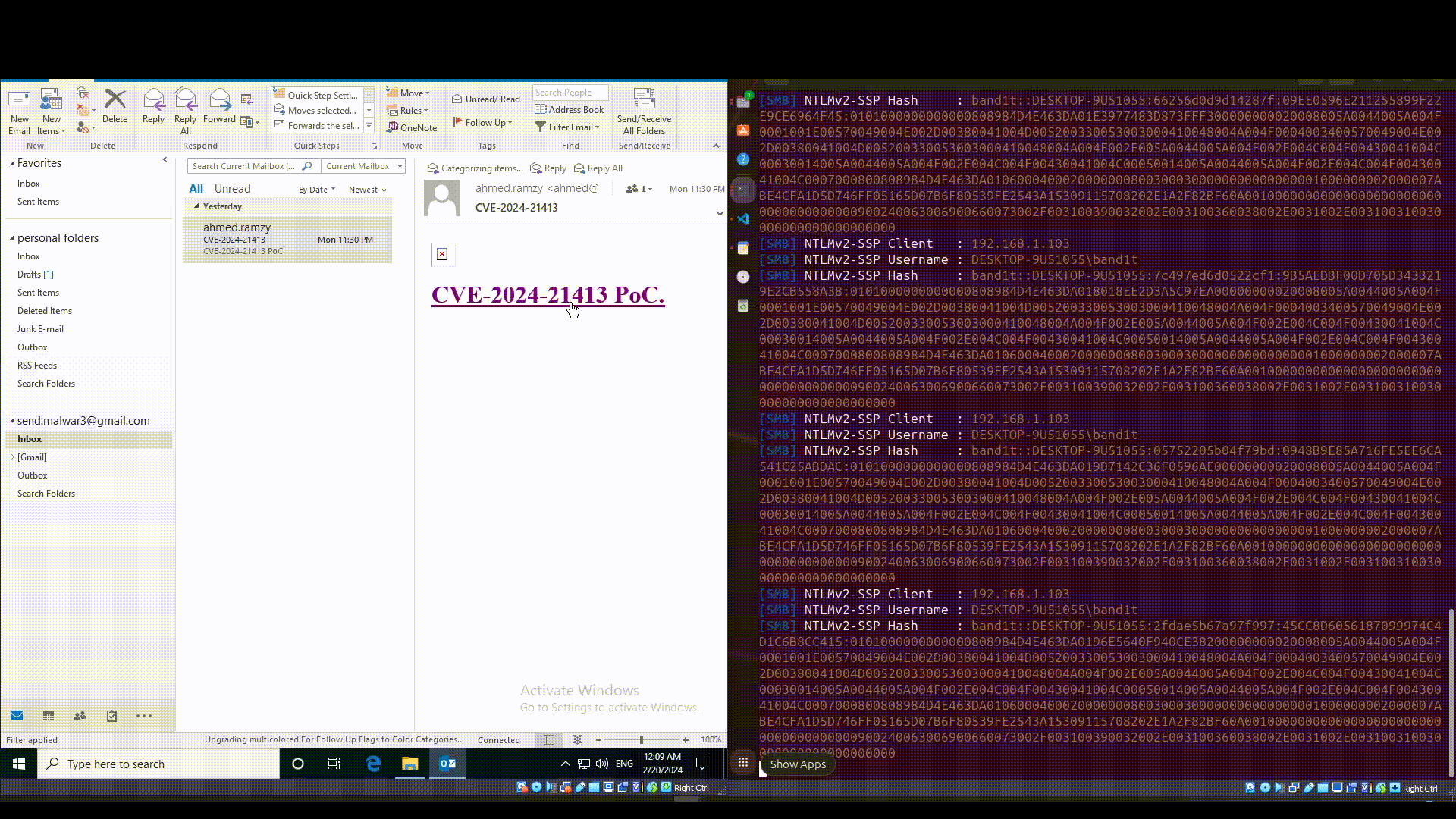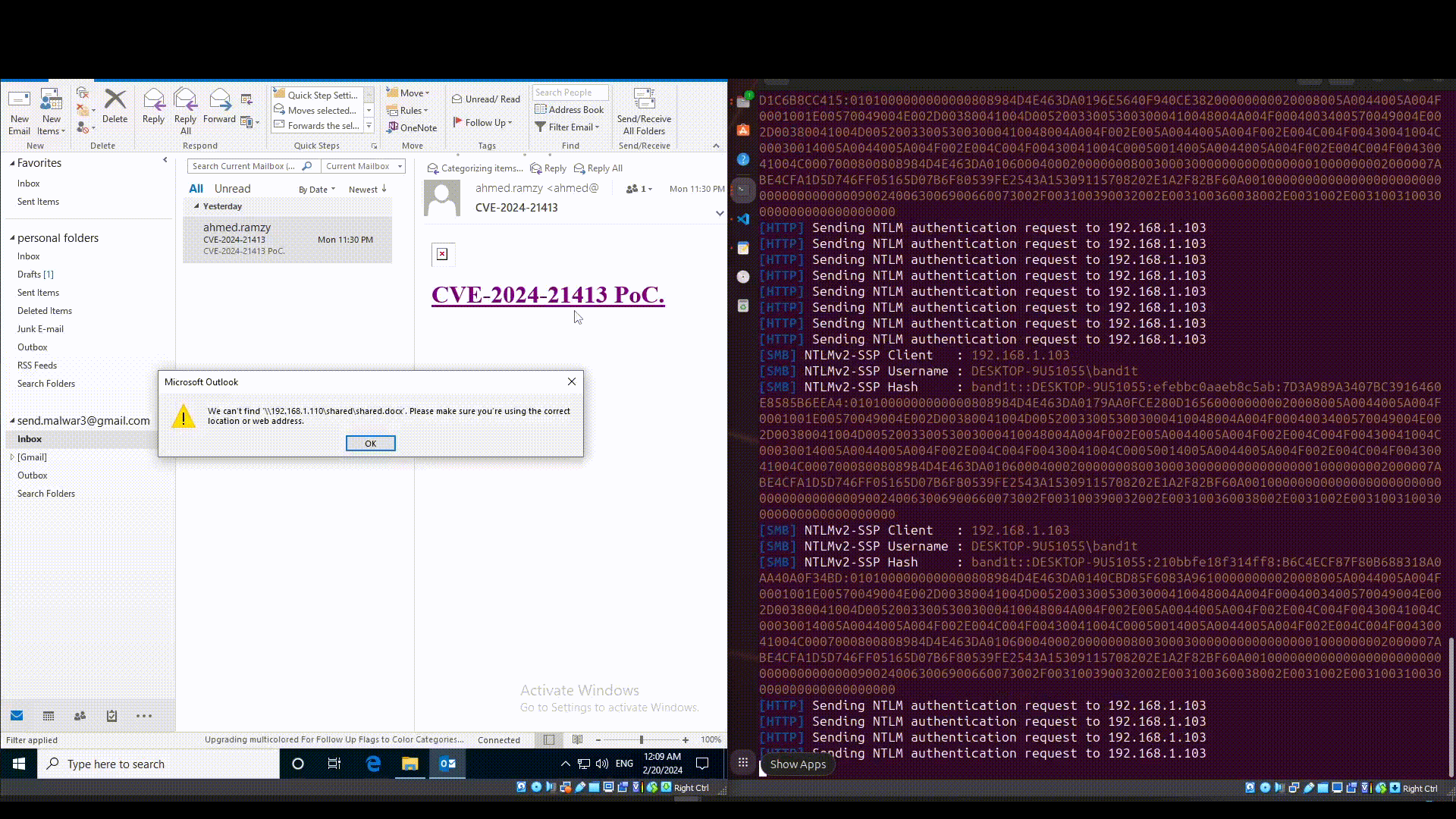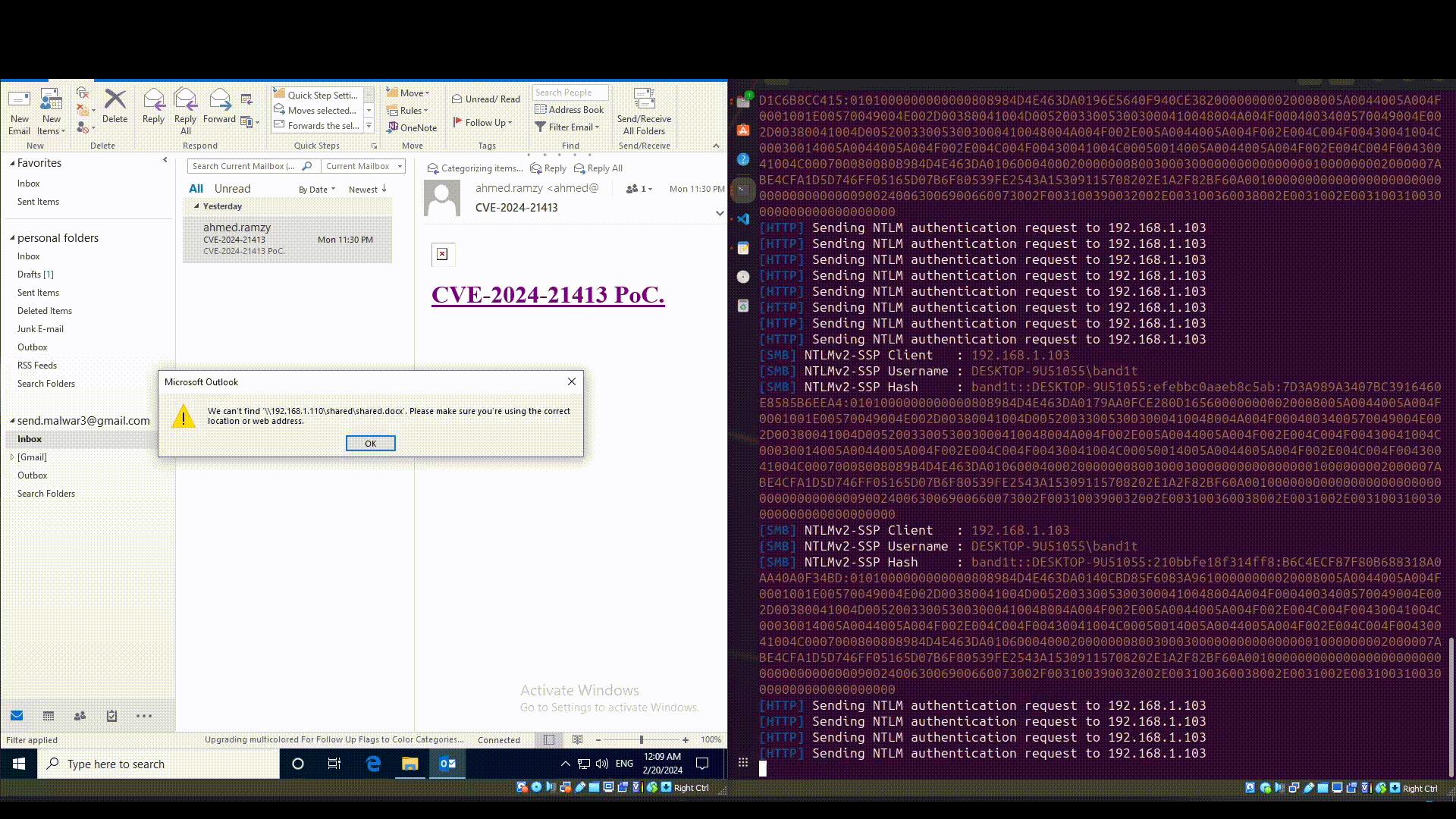
The threat does not stop at leaking the local NTLM credentials, as maliciously crafted payloads could lead to remote code execution. The attack depends on Outlook treating the malicious file URI as a Moniker string. The malicious link used is a composite moniker consisting of a file moniker and an item moniker. The file moniker locates a resource within a file system and depending on that resource a COM server is spawned to handle the resource.

The file moniker in this link identifies a Microsoft Office, docx, file and the item moniker identifies an object within that file. Since the identified resource is a docx file, Microsoft Office WORD application is spawned as a com server to load and parse the identified resource. A maliciously crafted docx file can exploit this process by forcing MS WORD to execute unsolicited actions. As a PoC of such attack, the follina vulnerability is utilized. The malicious moniker link provided by the attacker identifies a file that exploits the follina vulnerability by forcing MS WORD to execute arbitrary commands.
Note that follina, CVE-2022-30190, was patched by Microsoft and no longer works on newer systems; however, older systems are still vulnerable to the attack.

Risk
Detection
The cyber security R&D department at dPhish developed a new detection rule that automatically flags emails abusing this vulnerability. All clients of dPhish have automatically received the new detection rule.
The dPhish detection engine managed to flag the suspicious e-mail by looking for a file URI scheme that abuses the moniker bug. You can check the publicly available rule by dPhish here. It’s of critical importance to scan your network for any suspicious emails exploiting this vulnerability.


About dPhish
dPhish Suite is a comprehensive anti-phishing suite that aims to assess and enhance the company’s pre-, during, and post-phishing countermeasures by proactively evaluating and strengthening your human and technological defenses.
Using the dPhish suite, the company can benefit from a centralized portal to efficiently manage all phishing-related tasks. Gain insights about the gaps and guidance on resolving them which significantly reduces the risk of falling victim to phishing attacks.
Moreover, in the event of a successful phishing incident, the company will be empowered to respond promptly and gain visibility into any compromised credentials being traded on the internet or dark web.
